
Open-source intelligence, or OSINT, is a type of structured and enriched data that can help homeland security investigators uncover answers with speed and precision. Learn about OSINT types, tools, and methods to leverage in investigations.

In national security and defense investigations, answering the who, what, when, where, and why—the 5Ws—is important for better understanding threats and building actionable intelligence.
Open-source intelligence, or OSINT, is a type of structured and enriched data that may help investigators uncover these answers with speed and precision. It draws from vast volumes of publicly available data to illuminate relationships, timelines, and potential criminal intent.
However, OSINT may only be as effective as the methods and tools used to analyze it. Successful threat assessments and investigations—whether into terrorism, espionage, foreign disinformation, weapons proliferation, cybercrime, or critical infrastructure attacks—often combine OSINT with analytical tradecraft and top analysis platforms.
This guidance is designed to show intelligence analysts and fraud investigators how high‑volume OSINT can be integrated with risk data to support faster detection and intervention into suspicious activity.
- Start with a clear target
Security investigations should begin with clear targeting: which organization or individual do you aim to investigate, and what do you want to find out about them? It’s important to establish your investigative hypothesis at the outset, because you may discover along the way links to other entities with suspicious activity that distract from your original target. Before analyzing the additional risk scenarios that these connections surface, resolve your initial hypothesis.
Tools like Moody’s MaxsightTM Investigations can help you identify potential connections by displaying entities in a network map. As the map branches outward, stay focused on the paths that lead back to the central network node, in alignment with your original hypothesis.

In Maxsight™ Investigations, you may choose an individual or entity as a starting point for your investigation and enrich the data around the node.
- Identify unique identifiers for disambiguation
You may have already gathered internal data by the time you begin utilizing OSINT for your investigation. It can be helpful to verify a critical mass of unique identifiers from internal data to de-duplicate initial search results. For an individual, this may include their full name, other aliases, cities and countries of residence, one or two facial images, and date of birth.
For example, there may be many John Does and Jane Does with residences across Canada, the United States, and Mexico, so having multiple identifiers can help disambiguate OSINT data to provide a stronger research foundation. This may also help you stay ahead of counter measures that adversaries use to throw investigators off their scent, such as synthetic identities or the ownership of legitimate businesses alongside illegitimate businesses.
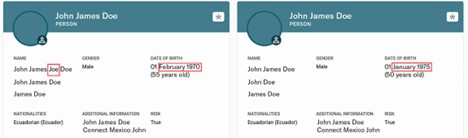
As seen in the Maxsight™ Investigations platform, multiple entities or individuals may have the same names or similar identifiers. You can compare detailed profile data to de-duplicate initial results before expanding your investigation map.
- Use high-volume OSINT to accelerate discovery
Despite its name, many in the intelligence community do not think of “open-source intelligence” as simply raw, open-source data that can be accessed on the web.
This is a common misconception: true OSINT is the result of transforming raw data into vetted, structured, and analyzed data. As a result of processing raw data into that which has been analyzed and classified for meaning and intention, OSINT reflects the second part of its name: “intelligence.” Importantly, OSINT seeks to remove the noise, or irrelevant data, from the signal, or intelligence, in the data.
Thus, OSINT can help to answer key questions in an investigation, because it transforms raw information from hundreds of thousands of online sources, such as government press releases and public records; news media articles; open-access academic and trade papers; websites and blogs; and social media posts, hashtags, and follows, into potentially relevant and actionable intelligence.
While free OSINT tools, such as search engines or AI chatbots, are widely accessible, it’s essential to understand how these tools source and manage data. Public domain information is generally permissible for use, but not all data is gathered responsibly or in accordance with legal standards.
In contrast, commercial OSINT providers operate within established data privacy frameworks like the European Union’s General Data Protection Regulation (GDPR), adhering to ethical standards, respecting terms of service, and ensuring proper data handling, which all supports provide compliant practices. These platforms also offer significant added value by verifying, organizing, and regularly updating data in centralized repositories, making it easier to access and analyze.
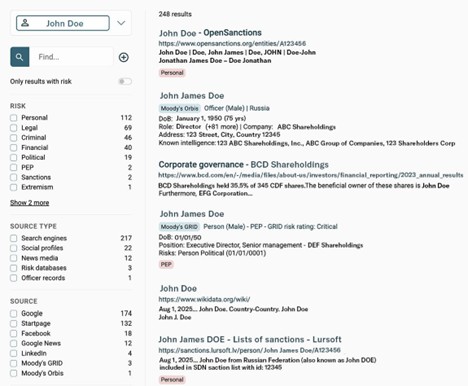
- Automate data enrichment and analysis
While OSINT data aggregators can provide investigators and analysts with access to large amounts of structured data on entities, it is important to find tools that can go one step further by displaying potential relationships between entities and types of risk associated with each entity.
Moody’s MaxsightTM Investigations platform can enrich data nodes within a network map, meaning it provides users with an option to populate the map with potentially connected entities using labeled arrows. The platform further enriches the data by highlighting potentially-associated entities, which can help analysts more quickly evaluate the level of potential risk associated with the original entity.
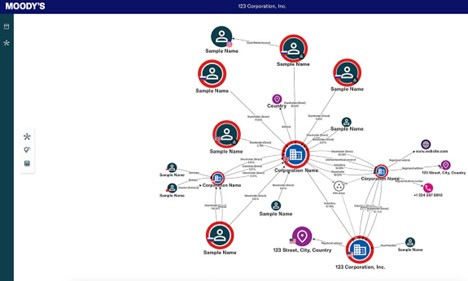
- Use intuition to lead the way
OSINT data aggregator and analysis tools can help accelerate an investigation, but an additional tool investigators and analysts should always have in their toolbox is intuition. As you investigate, your instincts as an investigator or analyst—founded upon years of training, repeated exposure to patterns, and deliberate practice—may be critical to the success of an investigation. In our age of AI and automation, the tools may be only as powerful as the users. It can be important to consider OSINT network data as a starting point, not a conclusion, and remain open to uncovering additional layers of risk through partnerships and analytic tradecraft methods.
Successful investigations are defined by OSINT access and tools
Large-scale OSINT data sources, together with precise OSINT analysis tools and traditional investigative methods, can provide the foundation for a successful investigation. Investigators and analysts can start with a strong hypothesis, followed by data disambiguation, open-source data aggregation, and reputable risk analysis tools.
How Moody’s can help
Moody’s provides actionable business activity intelligence that can help law enforcement agencies and corporate security professionals to better identify potentially nefarious behavior, as well as detect and track potential bad actors.
Maxsight™ Investigations is a platform that automates and centralizes investigation workflows so investigators can collect, view, analyze, and visualize vast datasets for faster results while maintaining analytical rigor.
In addition to providing the tool itself, Moody’s implementation specialists help integrate the tool into customer systems and can train customers on how best to use the platform.
Learn more about Maxsight™ Investigations.







